Infrastructure Design
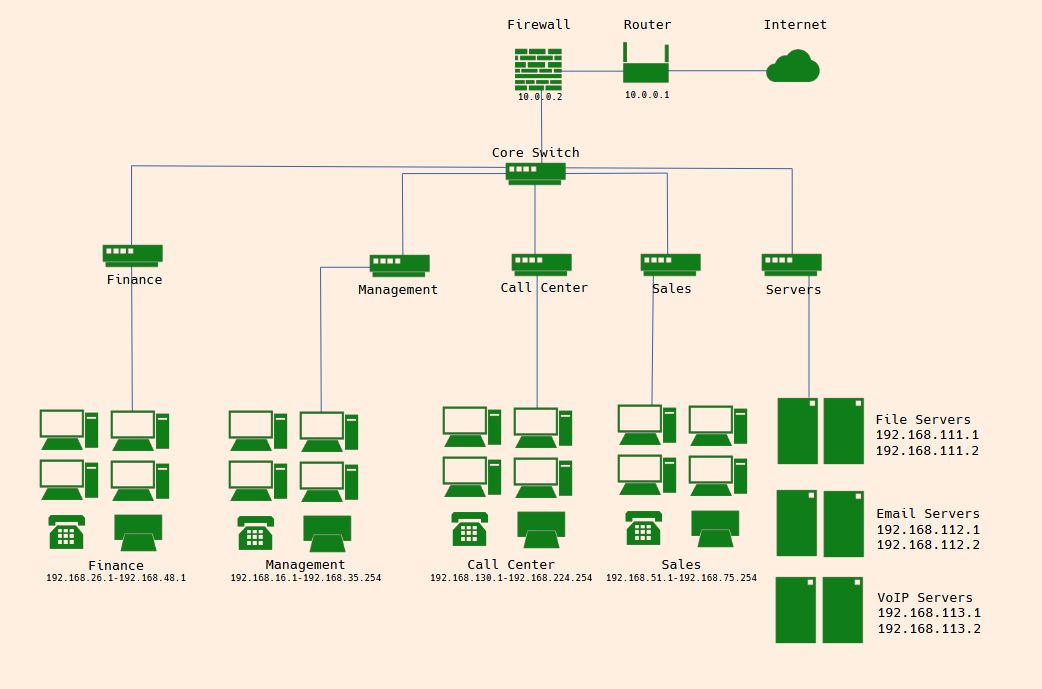
Network layout fulfilling the requirement of a fledgling network with room for expansion.
Download this document.

Network layout fulfilling the requirement of a fledgling network with room for expansion.
Download this document.
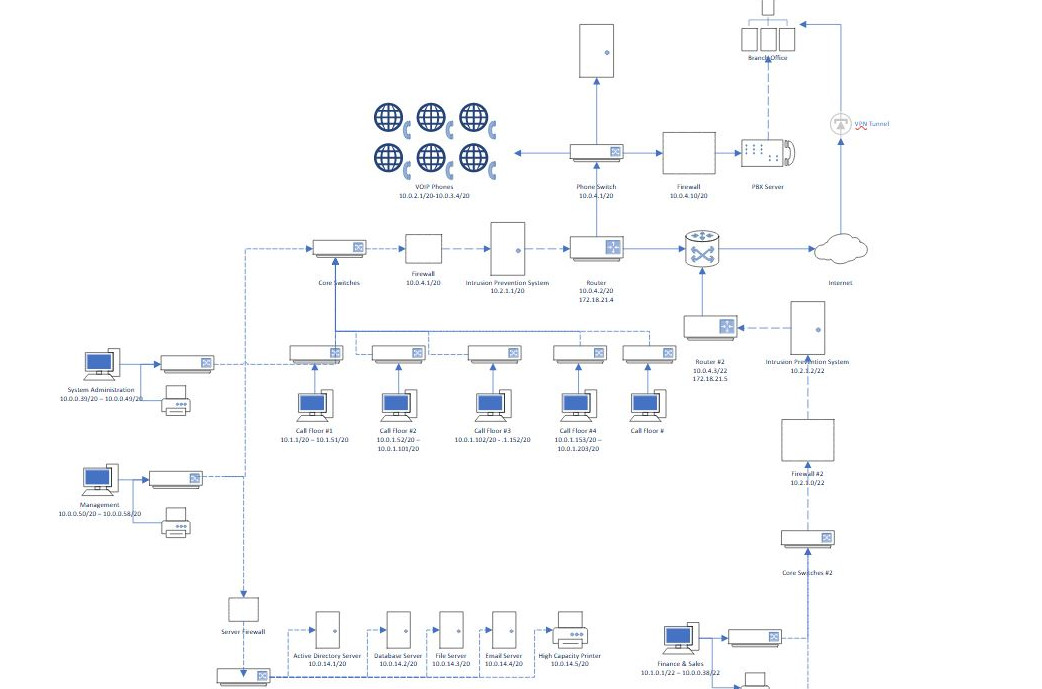
Layout made for Network Engineering, demonstrates implementation of Virtual LAN, Intrusion Detection/Prevention System.
Download this document.
Objective 2
Step-by-step explanation of the process of enabling Active Directory Domain Service.
Download this document.
Description of the process of creating redundant backup virtual machines in MS Azure.
Download this document.
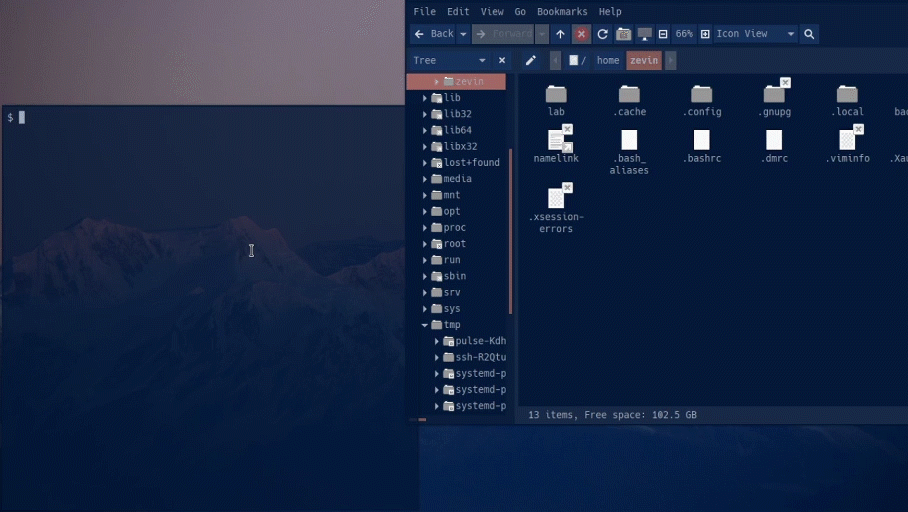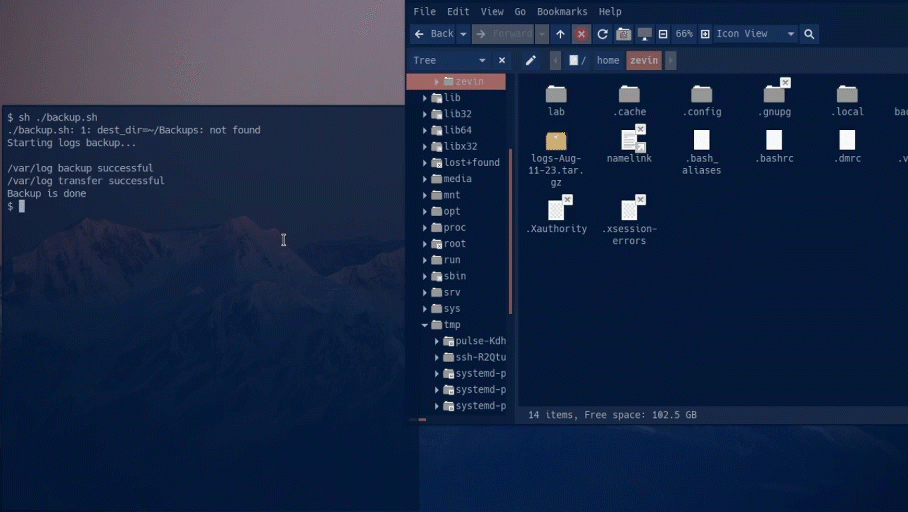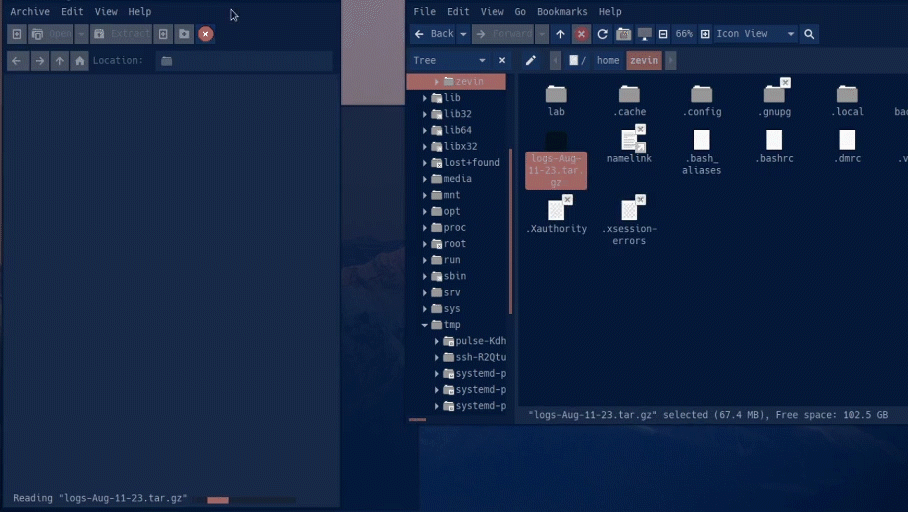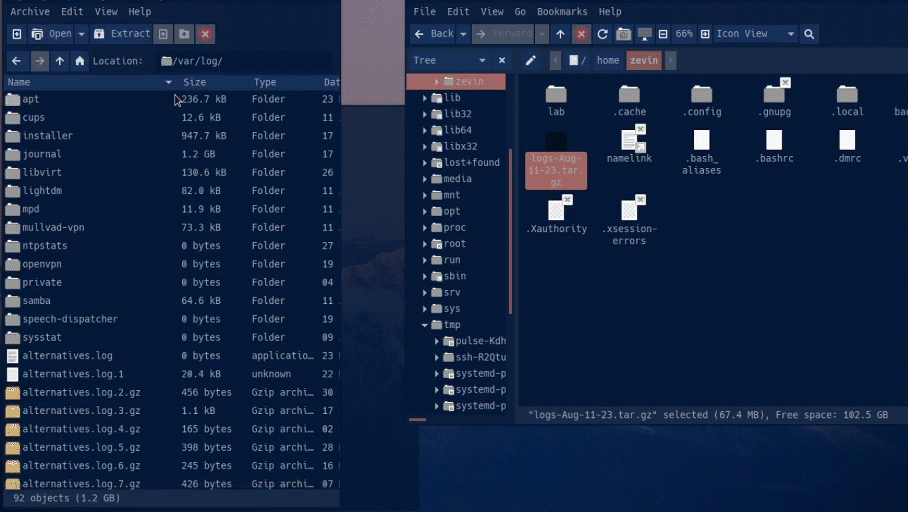
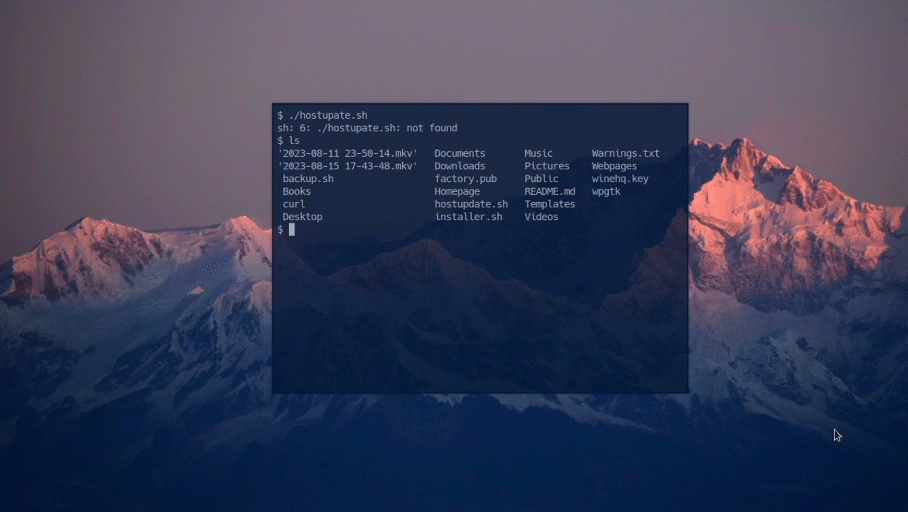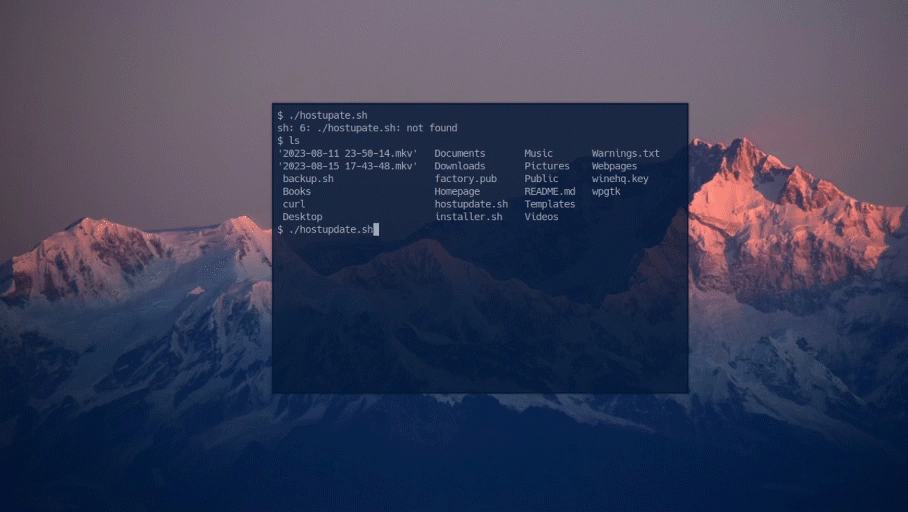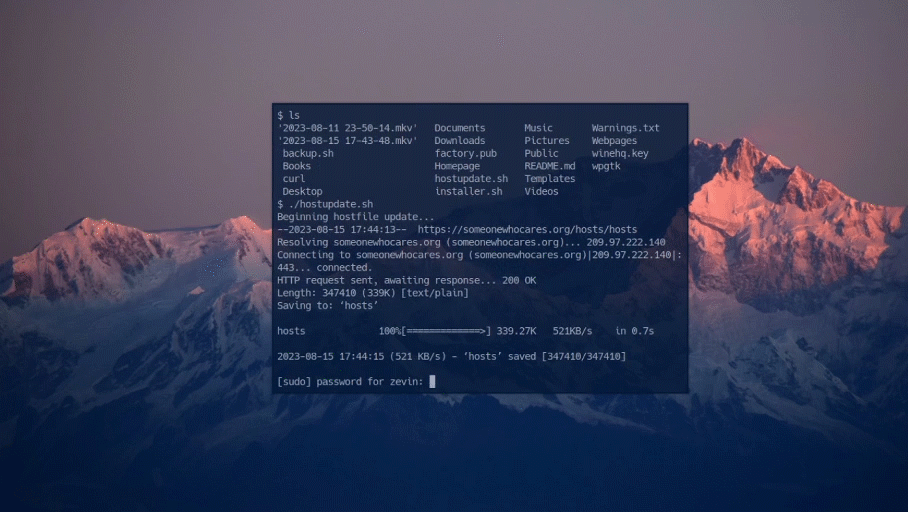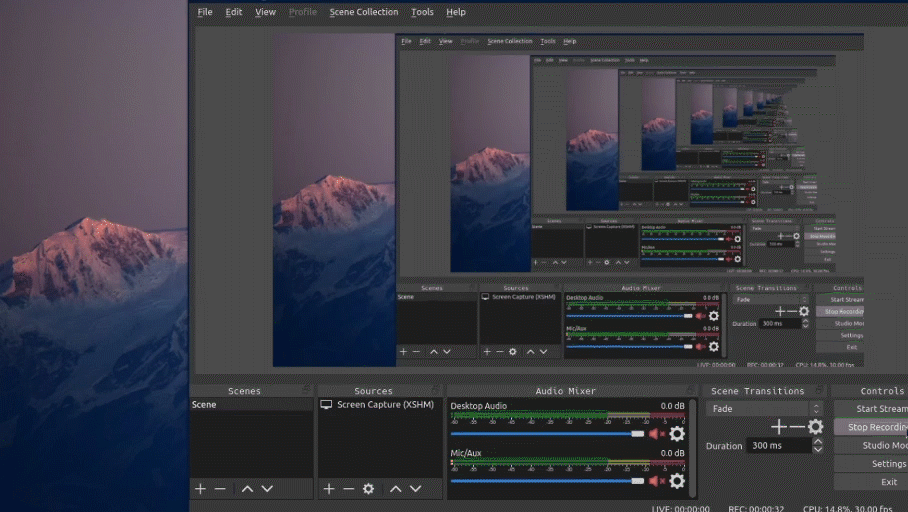
There are two scripts provided. The first shell script that backs up the logs inside /var/log. It archives them in a tar file with the corresponding date. The second script automatically fetches the most recent hostfile and puts it in the hostfile directory, this blocks new malicious ips.
View both of these scripts on github.
An instructional manual on company policy for what to do in the event of a disaster. Contains steps for evacuation, preventative measures, employee roles in the scenario, recovery process, and contact information for staff.
Download this document.
Calculations of the approximations of lost revenue from downtime of an organization's services. The intention is to highlight how dramatic the effects of an incident can be, even under good conditions.
Download this document.
Starting point for Ethics, being aware of ethical quandries and how everyone is capable of ethical failure. Important information before starting an organization and maintaining a conscience. A precursor to the Law and Ethics report of sorts.
Download this document.
Research report on what organizations should understand about the law. It's limitations, how it can benefit them, how they should respect it, as well as good ethical policies to ensure trust in the end user.
Download this document.
Presentation on an exploit in SMBv1 and SMBv2 file sharing functions that had a devastating effect on windows based systems in organizations.
Eternal Blue presentation here.